- Developers
- Developer Blog
- Software Development
- How to Make an Encryption Program?

profile

By Aran Davies
Verified Expert
9 years of experience
Aran Davies is a full-stack software development engineer and tech writer with experience in Web and Mobile technologies. He is a tech nomad and has seen it all.
Wondering how to make an encryption program like Boxcryptor? In this article, I explain what encryption is and how it works, provide examples of popular encryption tools and their use cases, and give a step-by-step guide on building an encryption program.
In this article
- Why Make an Encryption Program? The Premium on Data
- What Is Encryption?
- How Does Encryption Work?
- Different Types of Encryption
- Encryption and Regulation
- The Market Values Encryption
- Examples of Popular Use Cases of an Encryption Tool
- Popular Examples of Encryption Tools
- How to Make an Encryption Program?
- Frequently Asked Questions on How to Make an Encryption Program
The Cambridge Analytica scandal awakened many people to the importance of data security.
File encryption is a big part of keeping your personal data safe and out of the wrong hands.
Both individuals and enterprises are concerned about their data security. Building secure software products is a great way to make money and help prevent the misuse of private data.
If you need assistance developing an encryption program, contact a professional software development company like DevTeam.Space. Our experienced programmers will help you build a robust solution tailored to your needs.
Why Make an Encryption Program? The Premium on Data

Before we go deeper into building your own file encryption software, let’s first underline the importance of data. Some observers contend that data is the new oil. There is no doubt that it is the most important commodity in our digital era.
Read “The world’s most valuable resource is no longer oil, but data” if you want to learn more about this interesting observation.
A brief glance at world history shows us just how many conflicts took place with the sole objective of grabbing natural resources. It’s no wonder that similar conflicts are taking place over our data.
The armaments in this conflict aren’t weapons in the traditional sense; instead, the computer and complex big data analytics have become the main weapons!
Individuals acquire an increasing amount of confidential and sensitive data over the course of their lives. Today, we willingly provide this data to entities, including business organizations. We expect them to use it solely for the purposes we authorize them to.
However, as the massive Facebook-Cambridge Analytica data scandal shows, some unethical businesses do misuse our data. Then, there are hackers who just breach security mechanisms and gain access to our data. What can people do to protect their data? Answer: Encryption.
What Is Encryption?
Common people need a way to protect their sensitive data, even if it falls into unscrupulous hands. If the hackers can’t make any sense of the data, they will not have incentives to steal it in the first place!

Get a complimentary discovery call and a free ballpark estimate for your project
Trusted by 100x of startups and companies like
Encryption is the technology that turns our sensitive data into scrambled text. The process uses a secret code. Only you, having the secret code to turn that scrambled text back into meaningful information, can read your data.
Your data is secure as long as you secure that secret code! Read about it in “Encryption: what it is and Why it’s Important”. We call the process of converting the scrambled text back to the input data – “decryption”.
How Does Encryption Work?
Encryption isn’t new. Even ancient civilizations used it, although we wrongly consider their techniques and tools rather primitive now. Modern encryption uses mathematical algorithms. I will explain one such example, although remember that there are many ways to encrypt data.
Let’s review cryptographic hash functions, which are widely used in encryption. It works as follows:
- An input value is processed through an algorithm.
- The algorithm converts it into a scrambled text, which we call “hash”.
- Irrespective of the input value, a cryptographic hash function converts it into a fixed-length output.
- No two input values will have the same hash. Well, at least the probability of this will be truly minuscule!
- The algorithm works very fast.
- It’s incredibly difficult to convert the hash back to the input value without knowing the secret code.
A hacker, with access to only the hash value, will find it practically impossible to decipher the input. Read more about this algorithm in “Cryptography hash functions.”
Different Types of Encryption
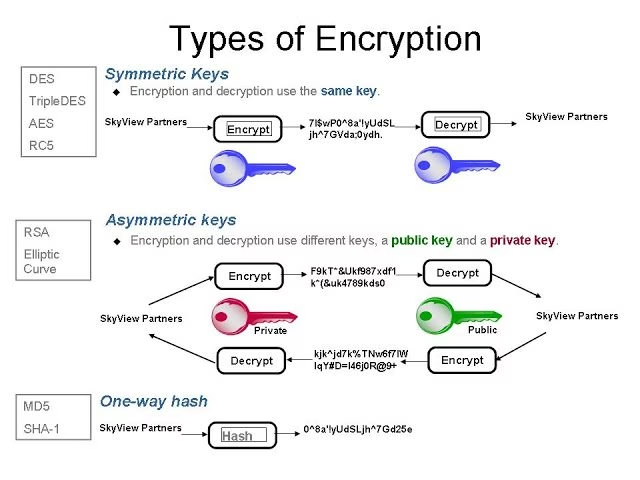
There are two types of encryption algorithms, as follows:
Symmetric-key algorithm
The symmetric key algorithm uses the same key for encrypting data as well as decrypting it. The sender of the message shares this key with the recipient. This is a secure algorithm if both parties secure the key, however, if a cyber attacker gets the key then decryption is easy.
Examples of this algorithm are as follows:
- “Format-Preserving Encryption” (FPE), where the input message and the scrambled text have the same format.
- “Advanced Encryption Standard” (AES) is a widely popular form of FPE.
Read more in “Types of encryption: What you need to know about underlying algorithms.”
Asymmetric algorithm
This type of algorithm is also called “Public Key encryption.” It works as follows:
- There are two keys: “Private key” and “Public key”.
- Users can share the public key, while they need to guard the private key. Bitcoin uses this type of algorithm.
- “Rivest-Shamir-Adleman” (RSA) algorithm is an example of an asymmetric type of algorithm. Here, the public and private keys are tied together using integer factorization of very large numbers. Hackers with today’s computers will likely take billions of years to find the private key from the public key. I have explained why in my article “Quantum Computing: will it kill blockchain?”.
Encryption and Regulation
People and businesses are aware of incidents where hackers have accessed personal sensitive data from some of the big data breaches covered in the news.
These events damage trust and have a serious downstream impact on the world economy. As a result, governments and regulators have responded with stringent regulations and data encryption requirements. I cite two examples as follows:
- The Health Insurance Portability and Accountability Act of 1996 (HIPAA) in the US has important data encryption requirements. You can read about it in “HIPAA encryption: What you should know”.
- “Payment Card Industry Data Security Standard” (PCI DSS) includes encryption as a key requirement. Read “PCI DSS requirement 3: what you need to be compliant” for more information.
These two regulations impact two heavily regulated industries, i.e., healthcare and payment cards. Note that governments and regulators have also enacted regulations for other industries requiring data encryption where data security is paramount.
The Market Values Encryption
Encryption, or “file encryption,” as many would call it, is an important building block in an organization’s information security strategy. Organizations must make considerable efforts to encrypt data in storage and while in transit.
If they are storing sensitive data in the public cloud, they need to encrypt it. Read more about the importance of encryption in “The Importance of Encryption: Some Things Never Change”.
The market certainly gives a “Thumbs Up” to encryption! Globally, the market for encryption software is growing at a CAGR of 14%, and it will be a US $ 8.4 billion market by 2024.
Read more about it in “Encryption software market size, share & trends analysis report by deployment, by application (disk, file/folder, database, web communication, network traffic, cloud), by end-use, and segment forecasts, 2018 – 2024”.
Examples of Popular Use Cases of an Encryption Tool
We now review a few popular use cases of encryption tools and algorithms, and these are as follows:
1. Securing sensitive communication and information in governments and militaries
All governments need to protect their interests against espionage attempts. With the advances in technology, espionage efforts have progressed far beyond human-centric operations. Government organizations like military forces need to protect their sensitive information.
Governments and militaries increasingly use encrypted files to exchange sensitive data. They also use strong encryption algorithms to secure their communication. Governments and militaries find 256-bit AES encryption as the best option for this since it’s the strongest encryption algorithm.
With the computing technology available in today’s market, hackers will require billions of years to crack an AES encryption algorithm that uses a 256-bit key. AES-256 encryption is that secure. We have explained this in “Quantum Computing: Will it Kill Blockchain?”.
2. VPN: Protecting privacy and security online
A VPN (Virtual Private Network) can protect the online privacy and security of users. They promise to prevent snooping and keep hackers at bay.
Hire expert developers for your next project
1,200 top developers
us since 2016
VPNs aren’t exactly new, and the VPN market is very competitive. Look for top-notch privacy and security features while choosing a VPN. A great VPN should consistently mask your IP address, however, it needs to do more!
Popular VPN providers like NordVPN use a robust encryption program to protect sensitive information that belongs to their users. Typically, they support 256-bit AES encryption. This encryption algorithm enjoys the reputation of being the most secure. VPNs sometimes offer other encryption too, e.g., AES-128.
Look for VPNs that don’t buckle under the pressure of governments to insert backdoors into their encrypted services. You should use a VPN that supports key platforms like Windows, Linux, macOS, Android, iOS, and routers. Great VPNs should also help you keep malware at bay.
3. Building a file encryption software
You can use an encryption algorithm to build a file or disk encryption software. Several such open-source software already exist, and we will talk about them shortly. One can encrypt data on computers and mobile devices using such software. You can even encrypt data in removable media and a flash drive.
Such software may have a wide range of utilities, e.g., encrypting a hard drive or individual files. You can use full disk encryption. Even if you lose your device, you have mitigated the risk of data breaches. Unauthorized personnel can’t read encrypted data on your device.
A file or disk encryption software uses an encryption algorithm to scramble data. Unauthorized people can’t decrypt these scrambled alphanumeric strings. Decryption is possible only with appropriate authentication, which requires encryption keys.
4. Securing business applications in heavily regulated industries
Cybersecurity is very important when you build software systems, and its importance is higher when you operate in a heavily regulated industry. Take the examples of banking and healthcare. Not only must you secure data at rest, but you need to provide real-time security to data in transit.
Encryption plays a key part here. A few examples are as follows:
- Endpoint encryption: An endpoint encryption software protects operating systems by preventing the installation of “Evil Maid” attacks. Software used in these attacks might install keyloggers, corrupt boot files, or lock files.
- Encryption of cloud storage: Cloud storage providers face a high risk of data breaches. They use encryption extensively to mitigate this risk, and you can find examples in Dropbox and Google Drive. Both encrypt data-at-rest and data-in-transit.
5. Cryptocurrencies
Cryptocurrencies like Bitcoin or Ethereum use blockchain, a technology that provides significant security benefits. Bitcoin and Ethereum don’t stop there, though. They use digital signatures to authenticate users.
A digital signature uses encryption extensively. It involves a public key and a private key. A Bitcoin user holds a cryptocurrency wallet; the public key is that wallet address. Someone intending to send Bitcoin needs to send it to this address.
The user must use a private key to sign a transaction, and that’s a secret. Users uphold the security of their accounts as long as they secure the private key.
6. Building a password manager
A password manager is a software that helps users to secure their passwords. Users don’t need to write down their passwords in a diary or remember them. Just set strong passwords, and you get the benefits of secure data. Password management software uses encryption, which does the rest.
Popular Examples of Encryption Tools
We now review the following popular examples of encryption tools:
1. VeraCrypt/ encryption software
VeraCrypt is a freeware utility software that provides “on-the-fly encryption” (OTFE). You can use it to create a virtual encrypted disk or encrypt a partition.
The creators of VeraCrypt forked TrueCrypt to create this utility. TrueCrypt has been discontinued. While VeraCrypt isn’t exactly an open-source software, its source code is available.
2. FileVault/ disk encryption program
Looking for an encryption tool on macOS, your favorite Apple platform? FileVault, a well-known encryption tool that provides OTFE is already available on macOS. This disk encryption tool can encrypt volumes on your Mac device.
3. BitLocker/ Windows encryption system
We talked about macOS, but what about an encryption tool on Microsoft Windows? Well, BitLocker does the job on Windows. This full-volume encryption tool is available in all Windows versions starting from Windows Vista.
4. AxCrypt/ file encryption software
So far, we have reviewed examples of file or disk encryption tools. Let’s review another type of software product that uses encryption. We are talking about password managers, and AxCrypt is a good example.
AxCrypt supports desktop and mobile devices. It provides strong encryption algorithms, including 256-bit AES encryption. In addition to password management, AxCrypt can automatically secure your files on Dropbox and Google Drive.
How to make an encryption program?
I will now take you through the steps to create your own file encryption software.
Step #1: Project scoping to make an encryption program
First, you need sufficient clarity of your objective, as follows:
- The objective is to build an app that will encrypt files.
- You are not trying to create a new encryption algorithm. I have already listed the standard encryption algorithms above.
- Creating a new encryption algorithm is not about computer application programming, rather it’s about mathematics. You need to have strong mathematics and statistics expertise; moreover, a new encryption algorithm requires stringent review to ensure it will be secure.
Read more about this clarity in this Quora Q&A thread.
Step #2: The development approach
You are likely launching an app to address a business need. Therefore, you are likely to want to focus on the business implementation side of things. As a result, an easy way to incorporate encryption in your app is a must!
I recommend you use the “Amazon Web Services” (AWS) encryption “Software Development Kit” (SDK). This enables you to implement encryption easily in your app. Read “What is the AWS encryption SDK?” for more details.
Hire expert developers for your next project
Step #3: Form a development team
Assuming you will create a mobile app for Android and a web app, you will need the following skills in your team:
- Business analysts;
- UI/UX design;
- Android developers;
- Web developers;
- Testers;
- A project manager (PM).
Web and mobile apps are “Systems of Engagement” (SoEs); therefore, iterative development is appropriate. The agile methodology supports iterative development. I recommend Agile software development for this project.
Read “How to build an Agile development team?” for more insights.
Step #4: Provision of a “Platform as a Service” (PaaS) for the web app
I recommend that you use AWS Elastic Beanstalk for your web app. This is the “Platform as a Service” (PaaS) offering of AWS. You have the following advantages with this approach:
- AWS Encryption SDK works seamlessly with AWS cloud platforms.
- You can focus on the software development, while AWS Elastic Beanstalk addresses the cloud infrastructure, networking, servers, middleware, operating system (OS), runtime environment, database, and 3rd party API integration.
Step #5: “Mobile Backend as a Service” (MBaaS) provisioning for the mobile app
You will need to provision a “Mobile Backend as a Service” (MBaaS) for the Android app. I recommend AWS Amplify, i.e., the MBaaS offering from AWS. You can focus on the mobile front-end design and development, while AWS Amplify offers the following advantages:
- It handles the cloud infrastructure, persistent storage, database, user management, push notifications, security, and 3rd party API integration.
- You can easily integrate the AWS Encryption SDK.
Step #6: Use AWS encryption SDK in your web and Android apps
AWS Encryption SDK offers the following features and advantages:
- It uses symmetric-key encryption. More specifically, it makes use of envelope encryption, where a master key further protects the data key for encryption. You can read more about it in “How the AWS encryption SDK works”.
- Since it uses the AES algorithm with up to 256-bit encryption keys, you have the assurance that your web and mobile apps are using industry-standard encryption techniques.
- AWS Encryption SDK is easy to use. You can use your AWS account for AWS Elastic Beanstalk and AWS Amplify anyway. A “Customer Master Key” (CMK) is needed; moreover, you need to create a user with an access key. You need to set your AWS credentials. Read “Getting started with the AWS encryption SDK” for more details.
- The SDK is available for Java and Python. For this project, you will need to use Java SDK. Visit “AWS Encryption SDK for Java” for installation instructions.
- As with other AWS products, you have excellent documentation for AWS Encryption SDK. Visit their “Frequently Asked Questions” (FAQ) page.
Step #7: Use AWS Elastic Beanstalk Java runtime for the web app
I recommend you use Java for creating your web app with file encryption on AWS Elastic Beanstalk. Read “Creating and deploying Java applications on AWS Elastic Beanstalk” for detailed instructions. Integration with the AWS encryption Java SDK will be easy.
Step #8: Use DevOps tools for the web app
Use an appropriate DevOps tool suite for the web app due to the following reasons:
- This will help in automated testing, build management, and deployment.
- Iterative development requires this “Continuous Integration” (CI).
I recommend you use the AWS DevOps tool suite. Read “DevOps and AWS” for more information.
Step #9: Use Android Studio for the mobile app
Use appropriate tools and guidelines for Android app development, as follows:
- Android Studio is the “Integrated Development Environment” (IDE) that enables you to code, test, and deploy easily.
- You will need to code in Java so that you can easily integrate the AWS encryption Java SDK. This guide provides instructions on how to code using Java in Android Studio.
- Read this guideline for deploying your Android app on “Google Play.”
Step #10: Use the “Scrum” technique to make an encryption program
Consider using the “Scrum” technique to manage this app development software project. A part of the Agile methodology, it works as follows:
- A cross-functional project team consisting of designers, developers, testers, and other roles takes the project forward. We call it the “Scrum team”, with the PM working as the “Scrum master”.
- “Product owners” provide the requirements or features in a document that we call the “Product Backlog”.
- Upon estimating, the team slots these into various “Sprints” according to the priority. “Sprints” are the iterations.
- The team uses a set of meetings, e.g., “Daily stand-up meeting” for status reporting, “Sprint review meeting” for gaining the project stakeholders’ approval, and “Sprint retrospective meeting” for learning lessons.
Read “How to build a Scrum development team?” for insights into “Scrum”. Use a robust PM tool. Trello is a good option for Agile projects, however, our guide “The 10 best Agile project management tools” has more options.
Planning to Make an Encryption Program for a Heavily Regulated Industry?
Are you planning to create an app for an industry with heavy data privacy regulatory requirements?
If so, you are going to need to build your own reliable file encryption software. Such a project to make an encryption program can become complex; therefore, consider engaging a professional development partner.
Our guide, “How to find the best software development company?” can help you find the right development partner.
If you are still looking for experienced software developers, contact DevTeam.Space and partner with our expert, vetted, and managed software developers community with the expertise to make an encryption program successfully using cutting-edge technologies for a competitive software market.
DevTeam.Space is an innovative American software development company with over 99% project success rate. DevTeam.Space builds reliable and scalable custom software applications, mobile apps, websites, live-streaming software applications, speech recognition systems, ChatGPT and AI-powered solutions, and IoT solutions and conducts complex software integrations for various industries, including finance, hospitality, healthcare, music, entertainment, gaming, e-commerce, banking, construction, and education software solutions on time and budget.
DevTeam.Space supports its clients with business analysts and dedicated tech account managers who monitor tech innovations and new developments and help our clients design, architect, and develop applications that will be relevant and easily upgradeable in the years to come.
Frequently Asked Questions on How to Make an Encryption Program
LastPass
VeraCrypt
FileVault
BitLocker
Read this article for our step-by-step guide on how to make an encryption program.
LastPass
Related Articles
Learn more about data security from our expert articles:
- Hire Web Developers Guide: 5 Best Companies 2025 (scroll down to read the article)
- Hire Mobile App Developers Guide: 5 Best Companies 2025 (scroll down to read the article)
- Enterprise Cyber Security – Why Enterprises Must Invest More in It?
- How to Build a Cybersecurity Mesh?
- What are the Top Fintech App Security Solutions in 2025?
- How to Build a Cybersecurity Software like Splunk?
- Best Cybersecurity Tools
- System Security Software – How Much Time Does It Take To Create One?
- Top 10 AWS Security Tips
- What are the Top Cloud Computing Security Issues for Businesses
- Drupal Security: How to Protect Your Website?

Alexey Semeney
Founder of DevTeam.Space
Hire Alexey and His Team To Build a Great Product
Alexey is the founder of DevTeam.Space. He is award nominee among TOP 26 mentors of FI's 'Global Startup Mentor Awards'.
Alexey is Expert Startup Review Panel member and advices the oldest angel investment group in Silicon Valley on products investment deals.