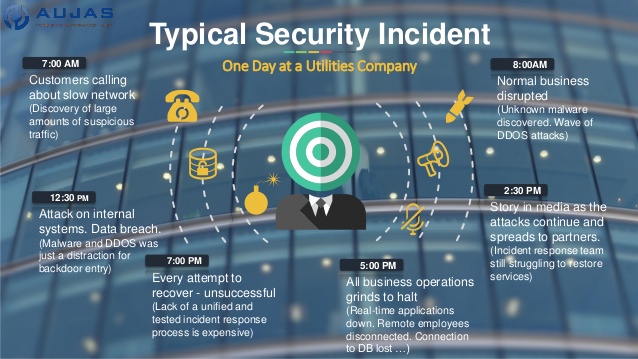
Enterprise Cyber Security – Why Enterprises Must Invest More in It?
Are you interested in knowing about enterprise cyber security and wondering why enterprises must invest more in cyber security solutions?
Read on as this is what we will answer in this article.
According to a study done by Verified Market Research, "Cyber Security Software Market was valued at USD 246.62 billion in 2024 and is projected to reach USD 497.05 billion by 2031, growing at a CAGR of 10.10%"
How Big Is the Problem of Cyber-Attacks?

A 2019 survey on businesses and charities in the UK shows the following:
- 32% of the businesses faced cyber-attacks in the preceding year.
- When you go one step deeper, you find that 60% of medium businesses and 61% of large businesses faced these attacks!
- 30% of the affected businesses had a loss of data or assets, and the cost to them was an average of £4,180 or $5,263 (at that time). The cost rose steeply from the corresponding figure in 2018, which was £3,160 or $3,979.
Read “Cybersecurity breaches survey” for more insights on this.

Get a complimentary discovery call and a free ballpark estimate for your project
Trusted by 100x of startups and companies like
Symantec, a cybersecurity provider offers alarming statistics in its 2019 Internet security threat report, e.g.:
- Cyber attackers load malicious code onto the retailer's website in a type of attack called "Formjacking", and steal the credit card details of shoppers. Formjacking impacts 4,800 websites every month, on average.
- Concerted efforts have curbed ransomware attacks, however, the problem persists.
- “Cryptojacking” attacks, i.e., hijacking unsuspecting users’ computers to mine cryptocurrencies, have reduced in 2018. This success came thanks to focused efforts, however, these attacks still take place.
- Malicious PowerShell scripts have increased by 1,000% in 2018!
- Cloud services providers face significant challenges. Cyber attackers stole 70 million records in 2018 from Amazon S3 buckets, exploiting faulty configurations.
- “Internet of Things” (IoT) devices are lucrative targets of cyber attackers, and almost every such device is vulnerable!
You can read the “Internet security threat report” to gain more information.
Cyber-Attacks Impose Enormous Costs on Businesses
The costs that businesses incur due to cyber-attacks are very significant. A few statistics can help in understanding this cost, e.g.:
- Data breaches can cost an average of $3.86 million per annum to businesses. It’s $7.91 million in the US, $4.74 million in Canada, and $4.67 million in Germany.
- The magnitude of data loss influences this cost. For example, each lost record can cost $148, whereas 1 million lost records cost $40 million. The cost reaches $350 million if the number of lost records surpasses 50 million!
You can find a more detailed report in “The average cost of a data breach is highest in the U.S. [Infographic]”.
The Hard Grind: Recovering From a Cyber-Attack or Customer Data Breach
Businesses incur massive costs due to cyber-attacks and data breaches, however, that alone doesn’t reflect the challenge fully. Consider the following:
- It takes 197 days on average to detect a data breach.
- On average, a business takes 69 days to contain the fall-outs from the data breach, and that's after detecting it!
- 75% of American consumers won't buy from a business if they think that the business didn't take the right steps to protect their data.
- The recovery from a data breach takes much longer if a malicious actor caused it, compared to incidents due to human errors. IBM found that identifying and containing breaches caused by malicious actors take 365 days on average.
You can read more about this in “IBM: A data breach will now cost your organization $3.86 million if you're lucky”.
What Is Cybersecurity?

Given the frequency of cyber-attacks and the cost, it's no surprise that businesses are turning to enterprise security solutions. Cyber security refers to protecting information systems from theft of data, damage to the system, and disruption to services they provide.
The broad objectives of cybersecurity are as follows:
- Protect systems connected to the Internet from cyber-attacks;
- Provide holistic protection, i.e., to hardware, software, and data;
- Analyze cyber threats proactively, and prepare to mitigate them;
- Continuously monitor the environment to detect threats.
Cybersecurity is a rather broad term, and it encompasses the following elements:
- Enterprise network security;
- Application security;
- Information security;
- “Disaster recovery” (DR) and “Business continuity planning” (BCP);
- Operational security;
- Comprehensive training for the users of computer systems.
You can gain more insights into “cybersecurity”.
The Market for Enterprise Cyber Security Solutions
The global market for cybersecurity solutions is growing steadily. The following statistics illustrate this growth well:
- The global cyber security market size was estimated at USD 245.62 billion in 2024 and is projected to grow at a CAGR of 12.9% from 2025 to 2030, according to a “Grand View Research” report.
- The global market for cybersecurity solutions will reach $300 billion in 2024, according to a PRNewswire projection.
- A “Cybersecurity Ventures” report projects that cumulative spending on cybersecurity will exceed $1 trillion during the 2017-2021 period. Market forecasts for cyber insurance policies range from $14 billion by 2022 to $20 billion by 2025.
Why Should You Invest More in Enterprise Cyber Security?
I will now explain why there is a need to invest more in enterprise cybersecurity. The reasons are as follows:
1. The rapid growth of data
The rate at which data is created has increased significantly, and the emergence of cloud computing is a key reason for this. Since cloud computing makes computing resources available to entrepreneurs without heavy upfront investment in IT infrastructure, this enabled rapid innovation.
Cloud computing gave big boosts to several technologies, e.g.:
1,200 top developers
us since 2016
- Mobile apps;
- Social media;
- IoT.
The result is an explosion in the volume of data created! You can understand this growth better, with the help of the following statistics:
- As of mid-2018, 2.5 quintillion bytes of data were created every day!
- 90% of the world’s data was created between mid-2016 and mid-2018, a rate that will only increase with the greater adoption of IoT. Read more about this in “How much data do we create every day? The mind-blowing stats everyone should read”.
- The world had a total of 33 zettabytes (ZB) of data in 2018, and this will grow up to 175 ZB by 2025, at a staggering 61% CAGR! Read about this estimate in "IDC: Expect 175 zettabytes of data worldwide by 2025”.
The growing volume of data will likely enable businesses to innovate more, however, this also represents a potentially bigger bounty for cyber-attackers! We can certainly expect cyber-attacks to increase, and this is a key reason why enterprises should invest more in cybersecurity.
2. The organized nature of cyber-attacks
We need to understand that cyber attackers are not "lone wolves". Cybercriminals are increasingly organized, and these organized groups operate in a coordinated manner.
For example, Comment Crew and Fancy Bear are two of the top hacking groups, and you can find more examples in "Top hacking groups impacting cybersecurity today”.
Cyber-attacker groups could belong to any one of the following categories:
- Hacktivists: They usually try to embarrass a government or another organization, as part of their campaign about an issue.
- Terrorists: Dreaded terrorist groups are all too willing to buy cyber-attack capabilities, however, their own internal capabilities are unknown at the time of writing this.
- State-backed hackers: These groups are some of the earliest cyber-attackers. They usually have the full backing of a state, therefore, their capabilities are higher.
Read more about these different kinds of cyber-attack groups in "Cybercrime and cyberwar: A spotter's guide to the groups that are out to get you”.
If you are still preparing to prevent that lone wolf cyber-attacker from hacking your enterprise IT systems. In that case, you need to acknowledge this change, and invest more in reliable cybersecurity solutions!
3. The ease with which cyber-attackers can launch attacks
Cyber-attackers have a very low entry barrier! The following quick facts illustrate this well:
- Cybercriminals can simply buy malware as a service on Dark Web forums.
- Malware that steals information is available in the form of pre-compiled binaries. There are also paid builder kits and even inexperienced cyber-attackers can easily use them to launch attacks.
- Spam botnets are quite affordable. For example, it only costs $200 for sending a million spam emails using a spam botnet called Kelihos.
You can read “Low-cost tools making cybercrime more accessible: SecureWorks" to learn more about how affordable cyber-attacks are. With such a low entry barrier, you can expect your enterprise to face more attacks, therefore, you need to invest in robust cybersecurity solutions.
4. The growing sophistication of cyber-attacks
Organized gangs of cyber-attackers never rest easy with the kind of tools they have at any given point in time. There is a coordinated effort to make cyber-attacks more sophisticated.
Cybercriminals use new tactics of attack, e.g.:
- Social engineering: These are manipulation techniques, e.g., phishing attacks. You can find more information on these techniques in “Sophisticated cyber attacks are the biggest technology concern”.
- Malware: These are malicious software that can damage organizations' information systems and computer networks. Cyber-attackers frequently launch new malware of different kinds.
- Ransomware: These are particularly damaging. Ransomware is malware, and cyber-attackers use them to threaten organizations. For e.g., the cyber-attacker might block access to information systems of high value, and then demand a large sum of money from the organization. You can learn more about these in “What is ransomware? How these attacks work and how to recover from them”.
You need to regularly upgrade your cybersecurity measures to deal with the increasing sophistication of cyber-attacks, and this requires a considerable investment.
5. The growth of IoT due to the 5G roll-out
At the time of writing, there are 26.66 billion IoT devices, and experts expect this number to reach 75 billion in 2025.
While there are many factors that contribute to the growth of IoT, one factor needs special mention. That factor is 5G, i.e., the fifth generation of mobile devices' communication networks. 5G will offer significantly higher bandwidth, much lower latency, and noticeably faster connection.
IoT will benefit substantially from the higher bandwidth offered by 5G since many more devices can be connected to IoT networks. A larger number of devices will enable businesses to extract greater value for their consumers.
With the growth in IoT, the security challenges will increase. By its very nature, IoT is vulnerable to cyber-attacks. The technology faces several security challenges, e.g.:
- Securing constrained devices;
- Authorizing and authenticating devices;
- Managing device updates;
- Securing communication between IoT devices;
- Guarding data privacy and data integrity.
This is not an exhaustive list, and you can read “Top 10 IoT security challenges” for more insights. If you are planning to utilize this promising technology to deliver higher value to your customers, plan to invest in robust cybersecurity solutions.
6. The growth of cloud computing
I have talked about how cloud computing boosted several other modern technologies, and now let’s talk about how cloud computing itself is growing. The following statistics can explain this growth well:
- The global market for cloud computing will grow from USD 445.3 billion in 2021 to USD 947.3 billion by 2026, at a Compound Annual Growth Rate (CAGR) of 16.3%, according to this report.
- Back in 2018, 85% of enterprises were already storing sensitive data on the cloud, and 67% of enterprise IT infrastructure and software will be on the cloud.
Cloud computing brings its own set of security challenges, e.g.:
- “Distributed Denial of Services” (DDoS) attacks;
- Data breaches;
- Data loss;
- Insecure access points;
- Lack of notifications and alerts in case of information security incidents.
Cloud computing offers undeniable benefits, and your enterprise must avail them. However, investing in a suitable cybersecurity solution is imperative.
7. Invest now in enterprise cyber security services, for a secure future!
Lastly, cybersecurity solutions are not that expensive when you consider the severe threats of cyber-attacks you face and their consequences. Investment in managed security services now will help you guard the reputation of the enterprise later.
Enterprise Cyber Security Needs All to Guard Against Cyber-Attacks
Preventing cyber-attacks is not the job of just a few people in the enterprise, rather, everyone needs to play his/her part. This requires a cultural transformation, in addition to a robust enterprise cyber security solution. We at DevTeam.Space can help you with such a transformation.
Write to us your enterprise cyber security requirements, and one of our account managers will get in touch with you to discuss more on how we can help via our field-expert software engineers community.
Frequently Asked Questions on Enterprise Cyber Security
This is any security solution that protects computer infrastructure and data from outside attacks, theft, or manipulation.
Most companies have several layers of cyber security including firewalls, virus and malware protection, as well as network access restrictions, etc.
There is no one-size-fits-all solution to cyber security. By far the most effective solution is to have layered protections in place that will prevent all but the most sophisticated attacks. Such solutions require expert advice and management.